Advanced Attacks against Internet Security Protocols
The Blavatnik ICRC Research by Prof. Shavitt and Dr. Demchak makes a global impact
The Blavatnik Interdisciplinary Cyber Research Center, Tel Aviv University (Blavatnik ICRC) facilitates world-class, leading interdisciplinary research. The Blavatnik ICRC Research conducted by Prof. Yuval Shavitt in 2016 on “Advanced Attacks against Internet Security Protocols”, not only created fascinating results but also evolved into a truly multidisciplinary study, combining research on Internet routing systems, anomaly detection and geopolitics of great power competition. Prof. Yuval Shavitt, from the faculty of Electrical Engineering at Tel Aviv University, studies Internet infrastructure and works on algorithms for the analysis of large graphs, IP geolocations, and protection of the Internet routing infrastructure. Dr. Chris C. Demchak, the RDML Grace M. Hopper Professor of Cyber Security and a member of the Cyber and Innovation Policy Institute, U.S. Naval War College, takes a systemic approach to emergent structures, comparative institutional evolution, adversaries’ use of systemic cyber tools, virtual worlds/gaming for operationalized organizational learning, and designing systemic resilience against imposed surprise.
The new article by Chris Demchak and Yuval Shavitt "China’s Maxim – Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking" is making headlines worldwide. The article has been downloaded 40,000 times in the first month, topping all other articles in the Military Cyber Affairs journal combined.
The authors first presented their research findings at the Emerging Technologies in Great Power Competition conference during CYBERWEEK 2018. We invite you to take a look at the video from the talk >>>
Highlights from the research:
Internet traffic travels through autonomous systems (AS) using the Border Gateway Protocol (BGP). Yuval Shavitt led the development of a special route-tracing system monitoring BGP announcements and capable of distinguishing abnormal patterns in Tel Aviv University. Working with Chris Demchak, they analyzed data from the system and uncovered several long-lived deliberate BGP hijacks that have hijacked traffic for a particular network, and have made it take a long detour through China Telecom's network in mainland China, before letting it reach its intended and final destination.
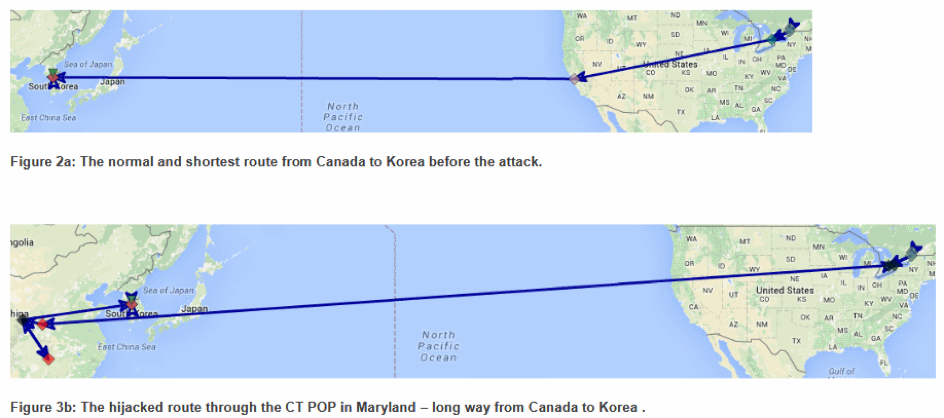
The report named four specific routes—Canada to South Korea, USA to Italy, Scandinavia to Japan, and Italy to Thailand—that were reportedly manipulated between 2015 and 2017 as a result of BGP activities of China Telecom. The authors concluded that the prevalence of and demonstrated ease with which one can simply redirect and copy data by controlling key transit nodes buried in a nation's infrastructure requires an urgent policy response. The publication attracted worldwide attention among IT-security experts, defence professionals and the general public.
Bruce Schneier, the internationally renowned security technologist, quoted the article when blogged on “China's Hacking of the Border Gateway Protocol and delivered the news to 250,000 subscribers. ZDNet article dedicated to the research was titled China has been 'hijacking the vital internet backbone of western countries'. Ars Technica of WIRED Media Group quoted the research in their Strange snafu misroutes domestic US Internet traffic through China Telecom piece: “While one may argue such attacks can always be explained by ‘normal’ BGP behaviour, these, in particular, suggest malicious intent, precisely because of their unusual transit characteristics—namely the lengthened routes and the abnormal durations,” the authors wrote. The Canada to South Korea leak, the report said, lasted for about six months and started in February 2016. The remaining three reported hijackings took place in 2017, with two of them reportedly lasting for months and the third taking place over about nine hours. After initial rebuttal, Oracle's Internet Intelligence division has eventually confirmed the authors’ findings.
Citation:
Demchak, C. C. and Y. Shavitt (2018). "China’s Maxim–Leave No Access Point Unexploited: The Hidden Story of China Telecom’s BGP Hijacking." Military Cyber Affairs 3(1): 7.
See also:
https://www.techspot.com/news/77129-researchers-discover-china-has-least-ten-pops-uses.html
https://www.hackerworldnews.com/china-hijacking-internet-traffic-using-bgp-claim-researchers/
https://boingboing.net/2018/10/26/bgp-pop-mitm.html
https://www.securityweek.com/china-telecom-constantly-misdirects-internet-traffic
https://www.itnews.com.au/news/china-systematically-hijacks-internet-traffic-researchers-514537
https://threatpost.com/googles-g-suite-search-and-analytics-traffic-taken-down-in-hijacking/139060/
https://venturebeat.com/2018/11/13/nigerian-telecom-fesses-up-to-routing-traffic-through-china/amp/
Making headlines worldwide:
- Australia: The Sydney Morning Herald How China diverts, then spies on Australia's internet traffic
- Germany: Die WELT Für 74 Minuten kapert China das Google-Netz
- Canada: The Globe and Mail China Telecom diverted internet traffic in U.S. and Canada, report finds
- Finland: TIVI
- Greece: https://katohika.gr/diethni/ti-megalyteri-kyvernoepithesi-stin-istoria-tis-dechtike-i-google/
- Nigeria: https://engineersforum.com.ng/2018/11/14/russia-and-china-attack-google/
- Czech: https://www.zive.cz/clanky/cina-mozna-roky-odposlouchava-podstatnou-cast-internetu/sc-3-a-195820/default.aspx
- Switzerland: https://www.nzz.ch/digital/google-datenpakete-auf-abwegen-ld.1436550
- UK: DailyMail
- Reuters: Nigerian firm takes the blame for routing Google traffic through China
“You can always claim that this is some kind of configuration error,” said Shavitt, who last month co-authored a paper alleging that the Chinese government had conducted a series of internet hijacks. http://news.trust.org/item/20181113175316-80rgd/
For media, inquiries contact Lior Tabansky, Blavatnik ICRC liort@tauex.tau.ac.il

